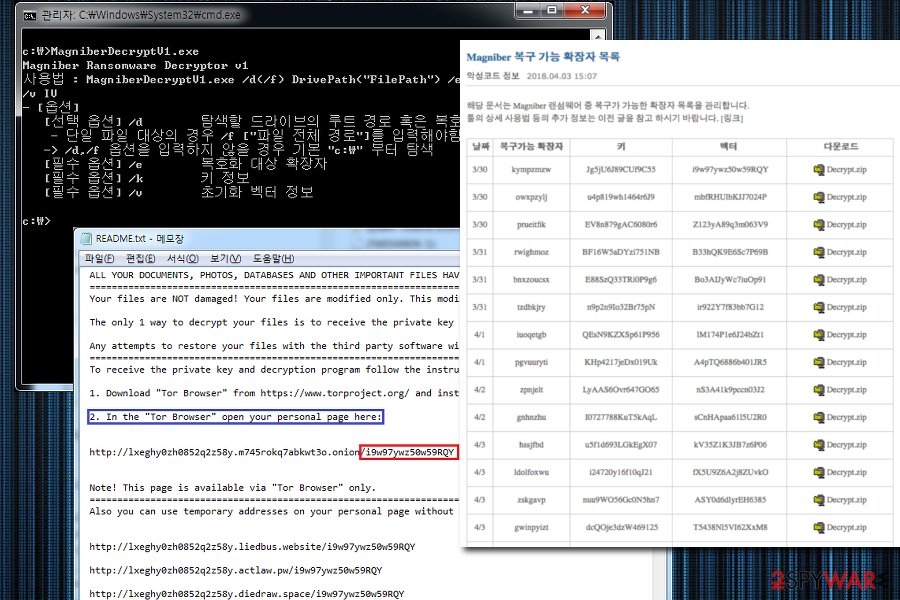
AhnLab’s new Magniber decryption tool renewed the existing tool in GUI format and now supports recovery for the parts that used to be unrepairable due to a variable vector found since April 8. However, it is limited to the case where encrypted/decrypted file exists as a pair with extension and key information. Expand Your Business through AhnLab Partner Program. Security Center. Security Insight. Security Risk Level. Find the latest threat intelligences direct from AhnLab’s security experts. AhnLab Solutions Portfolio. How to remove Magniber virus and restore encrypted files. This article is dedicated to ransomware called Magniber which gets onto customers' machines around the world, and encrypts their files. Here we've assembled full info on Magniber's essence, and the deletion of Magniber from your system. Initial samples demonstrate that Magniber only targets Korean-speaking users and, if it does not detect Korean language on the infected system, it will terminate its processes and not encrypt any files. If it does detect the Korean language, it will search for files to encrypt and append either. Kgpvwnr, or.dxjay to the file names.
- Distribution Method : Automatic infection using exploit by visiting website
- MD5 : bdb30eefb423d7710d45501b2849bfad
- Major Detection Name :Trojan/Win32.Magniber.R216865 (AhnLab V3), Trojan.Win32.MyRansom.114880856 (ViRobot)
- Encrypted File Pattern : .ygshc
Ahnlab Magniber Decrypt V4
- Malicious File Creation Location :
- C:Users%UserName%AppDataLocalREAD_FOR_DECRYPT.txt
- C:Users%UserName%AppDataLocalygshc.exe
- C:Users%UserName%Desktop<Random>.exe
- C:WindowsSystem32Tasksygshc
- C:WindowsSystem32Tasks<Random>
- C:WindowsSystem32Tasks<Random>1
Ahnlab Magniber Decrypt V4.1
- Payment Instruction File : READ_ME_FOR_DECRYPT.txt
- Major Characteristics :
- Offline Encryption
- Only run on Korean operating system
- Change the default values of the registry entry 'HKEY_CLASSES_ROOTmscfileshellopencommand' and disable system restore (wmic shadowcopy delete) using Event Viewer (eventvwr.exe)
- Auto execute ransomware (pcalua.exe -a C:Users%UserName%AppDataLocalygshc.exe -c <Random>) and payment instrucition file (pcalua.exe -a notepad.exe -c %LocalAppData%READ_FOR_DECRYPT.txt) every 15 minutes by adding Task Scheduler entries
- Auto connect MY DECRYPTOR site (pcalua.exe -a http://<URL>) every a hour by adding Task Scheduler entries